Customer Data Protection: A Marketer’s Guide to Securing User Data
Cybercrime is big business. In fact, research shows that cybercriminals bring in yearly revenues around $1.5 trillion by hacking data systems, stealing user data, and at times holding it for ransom.
Protecting customer data is more important than ever. Even something as simple as an email address is an example of customer data that needs to be protected. In fact, nearly every piece of customer data that a company collects and stores is something a cybercriminal might find valuable.
On top of protecting data from bad actors, companies also need to adhere to regional and evolving data privacy regulations to avoid fines, legal action, and a poor brand reputation.
Why is protecting customer data important?
Protecting customer data is important because your business depends on it. As we mentioned above, protecting customer data does more than safeguard your business from lawsuits and potential hacks, it also cements trust, and as a result, customer loyalty.
Equifax is a cautionary tale. Their data breach is one of the most well known of the 21st century. Overnight, the credit monitoring company lost $4 billion in market value. On top of that, they were fined $700 million by the FTC. Even years later, the company is still dealing with negative PR from the data breach.
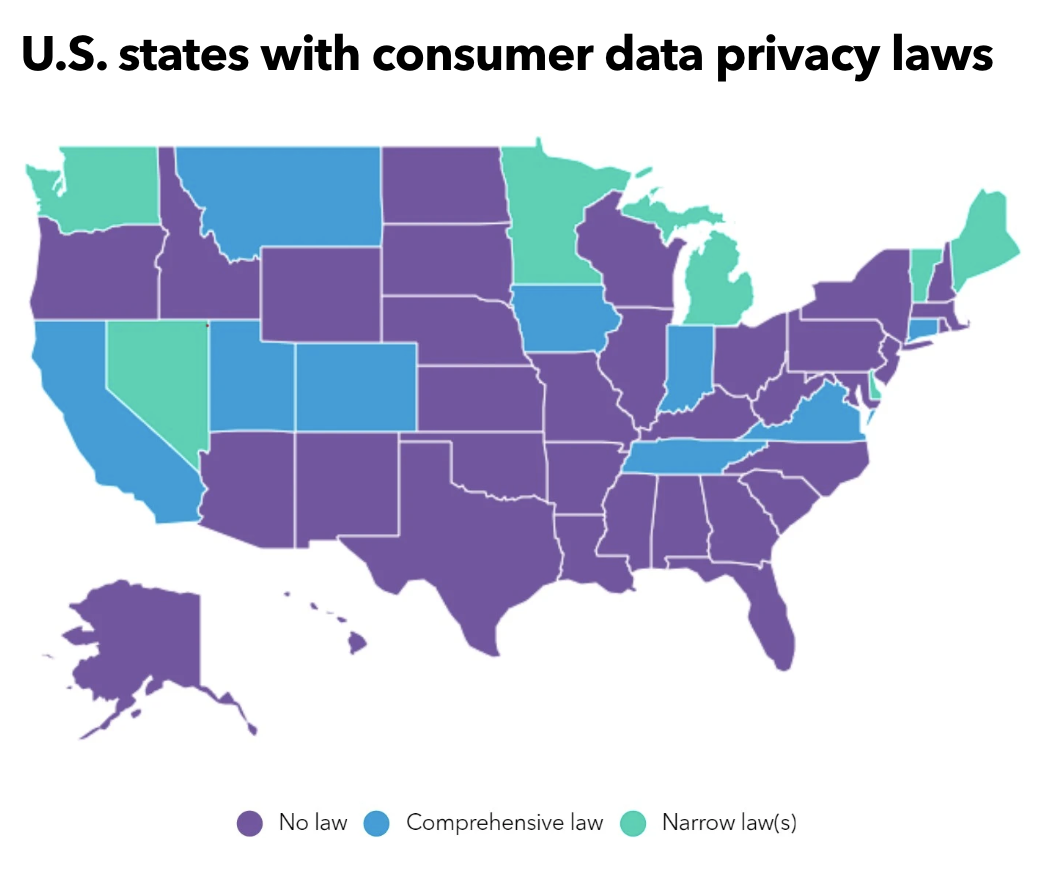
Laws like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) also require businesses to protect consumer data. Even if your business is not located in Europe or California, you may still be subject to these laws if your customers are residents. (The GDPR and the CCPA are the two most well-known regulations, but at least 25 states have data protection laws that also affect privately and publicly owned companies.)
8 steps to airtight customer data protection
We recommend the following eight steps to securing airtight customer data protection.
1. Only collect vital data
If you focus on only collecting data that is actually vital to your marketing efforts, you’ll do two things:
Decrease the external value of your data.
Increase consumer confidence.
Hackers are less likely to steal "low-value" data (e.g., if all a hacker has to gain from you is a list of email addresses, they might not put forth the effort).
But, if you’re collecting names, phone numbers, location data, household income, etc., then your data becomes more valuable. The greater number of data points that your company collects, the more valuable it likely is to outsiders.
Only collecting vital data can increase consumer confidence, too. When you’re collecting data that doesn’t seem necessary to the consumer, they might place less faith in your company.
Let’s say you go to download an e-book from a SaaS company. The form asks for the usual Name and Email Address, but it also asks for your ten other data points.
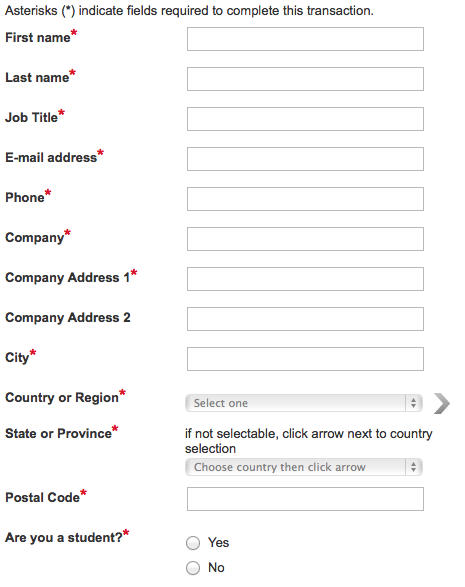
When you see a form with that many fields, it’ll probably cause you to question what that company really needs all that sensitive information for. As a result, you might be less likely to fill out that form because those two data points don’t seem relevant for downloading an e-book.
To evaluate what data is vital to your marketing team, periodically audit every piece of data you collect and ask, “If we didn’t collect this data point, would it drastically change the way we operate?” This is something that should be done at least once a year because, over time, you’ll start collecting unnecessary data without realizing it.
Auditing your data collection is a necessary step in ensuring your company is compliant with applicable Data Privacy Laws. Start by finding all the ways your company collects personal data about your customers. There are obvious places like website forms and analytics tools, but don’t forget about mobile apps and in-store data collection (if you have physical locations).
Let’s say your company’s main product is a CRM. Your product also includes a smartphone app that many of your customers use. Your app collects data about your users’ locations, texts, phone calls, calendars, contacts, and photos. When auditing your data, you need to look at each point of data collection and determine if it’s really necessary.
For your smartphone app, are all of the data collection points necessary?
The calendar data is probably useful for syncing the CRM to a calendar. But, what about user locations? Do you really need to collect that? Would not collecting it affect the way your business operates? Probably not.
2. Limit access to data
Not everyone on your marketing team needs access to all the data you’re collecting. Your employees also likely don’t need the same level of access to the tools they use.
Limiting access to data means there are fewer points of vulnerability for your organization. Each access point — where someone physically logs into a data analytics tool — is a point of weakness.
If you have 25 user accounts for your website analytics tool, that’s 25 points of vulnerability. If one of those accounts has a weak password, you’re leaving your entire system open to a brute-force attack.
Having fewer employees with access to your customer data also reduces the risk of internal data abuse. For example, let’s say you have to fire an employee but they have access to so many SaaS tools that you're actually not even sure of the full list. You cut off their use to ten tools, but you forgot one. They go home and access that tool from their home computer because the data is stored in the cloud. Now, they can do whatever they want with it.
Had you just limited their access to only the tools they needed, you would have had a better understanding of which tools you needed to cut off.
3. Use password management tools
As we mentioned above, access points — or the login point — are always going to be a vulnerability. You can boost your cybersecurity and reduce the risk of hacks happening here by requiring all employees to use a password management tool.
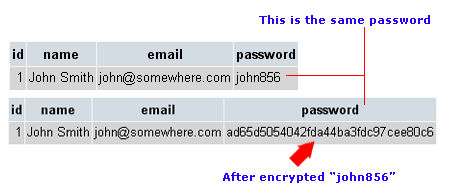
These tools create and store complex passwords for all of the tools and software that your team uses. Typically, people won’t use complex passwords because they’re too hard to remember. Password management tools make that much simpler by encrypting and storing each password. That way, when someone needs to log in to a tool, they’ll be able to easily pull the login information from the password manager.
Good password management tools use complex encryption for the passwords they store. Encryption makes the password unreadable to anyone without the encryption key. That means if a hacker breaks into your password management tool, all of the passwords will be unusable because they'll be unreadable to the hacker.
Password management tools are even more valuable when your team uses just one login for a specific tool or piece of software. When this happens, teams typically create an easy to remember password and share it with everyone who needs access. There’s no doubt that handling shared passwords that way without further authentication is a massive vulnerability.
A password management tool can make shared logins more secure by storing this login information and giving access to people who need it, without those people actually knowing the login information.
That way, if someone leaves the company, they won’t be able to log in to that tool because they never had the password in the first place.
Password managers also give you a way to easily shut off access to all tools if someone exits the company. Once the employee leaves your company, you can shut off access to the password manager and the user won’t be able to login to any of the other tools they use.
Then, once you’ve done that, you can shut off access to each individual tool, just in case. This reduces the likelihood that you’ll forget to cut off access to one tool. As you can see password managers really go a long way in protecting customer data.
4. Avoid data silos
Data silos aren’t just bad for data analysis; they can also lead to significant vulnerabilities.
Data silos often mean that different pieces of data are being stored in different places. This can lead to data being stored in non-approved, unsecured applications. It also might result in you losing track of where certain data is stored. If you lose track of where certain data is stored, you might not even realize when you have a data breach.
When you break down data silos, you’ll develop a customer data management strategy. That data management strategy will detail exactly where and how data is handled. That prevents you from storing data in multiple tools, and losing track of what tools you use to handle data.
When you work to eliminate your data silos, you’re also going to use a data tracking plan. This plan helps you keep track of what data you’re collecting and why you’re collecting it. That’ll make your data collection audits, that we mentioned in Step 1, much simpler.
5. Make sure third-party vendors and partners are also protecting customer data
Your data is only as secure as the tools you’re using. If you’re using a SaaS tool that handles some of your data, but that tool isn’t secure, your data could be vulnerable.
Anytime you’re considering adding another tool to your marketing stack, evaluate that tool’s security standards. If the tool isn’t as secure as possible, your data isn’t as secure as possible.
Make sure any tool you use complies with either SOC 2 or ISO 27001. Both of those standards require companies that comply with them to continuously monitor and upgrade their data security protocols.
For the tools you’re currently using, double-check their security standards. If they’re not using SOC 2, or ISO 27001, consider finding a more secure alternative.
6. Conduct regular security audits and assessments
Having the right framework in place to protect data privacy is step one. Step two is avoiding complacency by regularly conducting security audits and assessments to identify any new or potential threats. First, set a standard as to how regularly you’ll conduct a security audit (e.g., annually), and what its scope will be (e.g., the systems you’ll be reviewing). Here’s a broad checklist of what should be done during a cybersecurity audit or assessment:
Know your baseline. What current security measures are in place? What data are you currently collecting, and where is it stored?
Check access permissions and controls. Which data do different teams and users have access to? Are the proper permissions in place to protect highly sensitive data?
Run through your protocols for incident response (e.g., how are threats detected and dealt with?)
Review your relationship with third-party vendors, and if they have access to your company’s customer data.
Review and understand applicable privacy laws and regulations (e.g., regional data residency, CCPA, Payment Card Industry Data Security Standard or PCI DSS, HIPAA)
Report on your findings to key stakeholders, along with recommendations for any updates or next steps.
7. Employee training and awareness
Effective data protection requires company wide buy-in; that is, every employee needs to be informed about regulations and best practices. Educating team members on cybersecurity threats, like phishing schemes that trick employees into giving away their credentials, is of the utmost importance.
You might also consider assigning someone to oversee data privacy, like a Data Protection Officer.
For more information on how to educate team members on data security, we compiled this list of 16 training resources as a starting point.
8. Review compliance with data protection laws
Laws and regulations surrounding data privacy and protection are there for a reason, and it's important every business understands what these laws entail (and which ones they’re subject to). For instance, even companies that may be based in the U.S. have to comply with the GDPR if they handle data from customers in the EU.
(The GDPR put together a compliance checklist for US companies, as a helpful resource.)
What are the risks of not protecting customer data?
Not protecting customer data is a risky endeavor, endangering everything from your company’s operations, to its brand reputation, and of course the subsequent legal and financial fallout. Below, we cover the more notable risks of taking a lackadaisical approach to data privacy and security.
Cybercrime
As we mentioned above, cybercrime has become a popular and lucrative business, and companies need to be diligent about protection and prevention. A few of the most common types of cybercrime attacks include:
Phishing. This is usually done by sending an email to an employee at an organization, tricking them into giving sensitive or confidential information. “Whale-phishing” is when these types of attacks specifically target a top executive or C-suite member.
Distributed Denial of Service (DDoS). This is when cybercriminals try to overwhelm a server or network by flooding it with internet traffic.
Trojan Horse. This is when malware is presented as a legitimate program that a user accidentally downloads.
Business interruption
When a business deals with a cyberattack of data breach, its operations can come to a screeching halt. DDoS is a perfect example of this, essentially creating an online traffic jam so that the site becomes unavailable or sluggish to real customers.
Legal liability and financial loss
Protecting customer data is more than just an ethical issue, it’s a legal one. If a business fails to comply with applicable privacy regulations, they could find themselves facing a lawsuit and usually a financial repercussion.
Instagram is one example; the company was fined $403 million by Ireland’s Data Protection Commissioner after it was accused of violating the GDPR in regard to children’s privacy.
Reputational damage
One of the lasting effects of non-compliance with data privacy laws is: reputational damage. For instance, the consulting firm Cambridge Analytica became infamous for its data scandal in 2014-15, in which private data from Facebook users was used to create voter profiles.
How to minimize the consequences of a data breach
The best way to minimize the impact of a data breach is to prevent it altogether, instituting policies and best practices like:
Only collecting customer data that is vital to business operations.
Tracing data lineage and using data mapping to understand how data is stored within your organization (e.g., its original source, where it currently lives, who has access to this data).
Implementing data governance controls like user-based access to highly sensitive data and automatic data masking.
Regularly auditing data and reviewing data privacy laws to ensure compliance.
However, if a data breach has occurred, there are ways to mitigate the fallout. The Federal Trade Commission (FTC) recommends acting fast. You should have a plan in action in place to respond to a potential data breach, like immediately locking down access to certain operations and systems and consulting with legal counsel. You’ll also likely need to report the incident to both customers (if their data was at risk or leaked) and law enforcement.
Protecting customer data is vital to your business
Customers trust you with their most sensitive data, from credit cards to Social Security information, and it’s your responsibility to keep it secure. There’s never been a better time to take steps to protect your customer data with a CDP. If you’ve never evaluated your data protection practices, or it’s been a while since you've done it, these eight steps that we outlined are a good place to start.
Frequently asked questions
Segment's Privacy Portal
With the Segment Privacy Portal, you can automate your approach to keeping your customers' data private.
Get started
Additional Resources
Getting started is easy
Start connecting your data with Segment.